In the world of computer networks, the OSI Model stands as a guide that standardizes communication between systems. Whether you’re troubleshooting a network issue or studying for certifications like CCNA, understanding the OSI Model is essential
What is the OSI Model?
The OSI (Open Systems Interconnection) Model is a conceptual framework developed by the International Organization for Standardization (ISO). It standardizes the functions of a telecommunication or computing system into seven abstraction layers, enabling different systems to communicate using standardized protocols.
The OSI Model helps break down complex network interactions into manageable parts.
Although, we don’t need it today, but the reason that OSI Model is still being used is just for troubleshooting purposes.
It is used to know that what error happened while transferring the data.
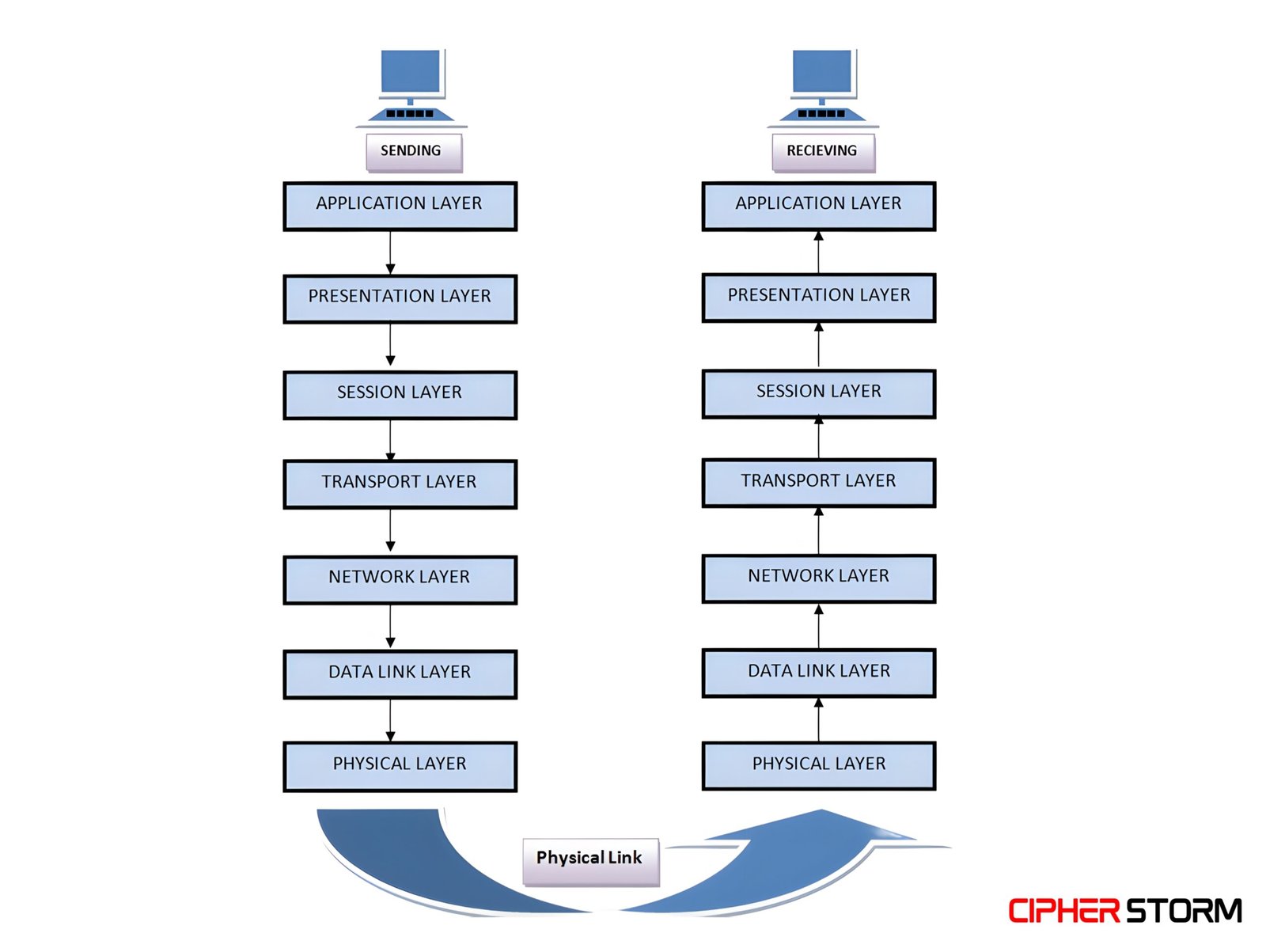
The 7 Layers of the OSI Model (Top to Bottom)
7. Application Layer
- Function: Closest to the user; enables user interaction with applications.
- Responsibilities:
- Network services like file transfer, email, web browsing.
- Interface for software applications.
- Examples: HTTP, FTP, SMTP, DNS, POP3
- Devices Used:
- Web Servers,
- Proxy Servers
- Application Firewalls
- Possible Attacks:
- SQL Injection (injecting malicious SQL queries)
- Cross-Site Scripting (XSS) (injecting scripts into web pages)
- Phishing (deceptive websites or emails stealing credentials)
6. Presentation Layer
- Function: Translates data formats between sender and receiver.
- Responsibilities:
- Data encryption/decryption
- Compression/decompression
- Data conversion (e.g., ASCII to EBCDIC)
- Examples: JPEG, MPEG, SSL/TLS
- Devices Used:
- Encryption Devices
- Data Compression tools
- Possible Attacks:
- Code Injection attacks (malformed data causing application faliure)
- Data Manipulation attacks (tampering with encrypted or decompressed data)
5. Session Layer
- Function: Manages sessions between applications.
- Responsibilities:
- Establish, maintain, and terminate communication sessions.
- Dialog control and synchronization.
- Examples: NetBIOS, RPC, PPTP
- Devices Used:
- Gateways
- Firewalls
- Session Monitors
- Possible Attacks:
- Session Hijacking (stealing an active session)
- Man-in-the-middle (MITM) attack (intercepting and modifying session data)
4. Transport Layer
- Function: Ensures reliable data transmission.
- Responsibilities:
- Segmentation and reassembly of data
- Flow control
- Error correction
- Examples: TCP, UDP,SCTP
- Devices Used:
- Firewalls
- Intrusion Detection Systems (IDS)
- Possible Attacks:
- Port Scanning (identifying open ports for exploitation)
- SYN Flood attack (overloading a server by sending excessive TCP requests)
- Session Hijacking (taking over an active TCP session)
3. Network Layer
- Function: Handles routing and logical addressing.
- Responsibilities:
- Path determination
- Logical addressing (IP addressing)
- Packet forwarding
- Examples: IP(IPv4, IPv6), ICMP, IPSec, RIP
- Devices Used:
- Routers
- Layer 3 Switched, Firewalls
- Possible Attacks:
- IP Spoofing (forging source IP to impersonate another device)
- DDoS (Distributed Denial of Service) (overloading a network)
- Routing attacks (manipulating routing tables, BGP hijacking)
2. Data Link Layer
- Function: Provides node-to-node data transfer.
- Responsibilities:
- Error detection (not correction)
- Framing
- MAC addressing
- Examples: Ethernet, PPP, Switches, MAC Address, IP(IPv4, IPv6)
- Devices Used:
- Switches
- Bridges
- MAC Addresses
- Possible Attacks:
- MAC Flooding (overloading a switch’s MAC table)
- ARP Spoofing (impersonating another device on the network)
- STP (Spanning Tree Protocol) Manipulation (causing network loops)
1. Physical Layer
- Function: Transmits raw bit stream over the physical medium.
- Responsibilities:
- Cables, signals, voltage levels
- Hardware like NICs and Hubs
- Examples: Fiber optics, Coaxial cables, Hubs, Modems
- Devices Used:
- Hubs
- Repeaters
- Cables (Coaxial, Fiber Optic, Twisted Pair), Network Interface Cards (NICs
- Possible Attacks:
- Wiretapping (eavesdropping on physical connections)
- Jamming (signal interference)
- Physical Sabotage (damaging cables or devices)
Mnemonics to Remember the OSI Layers
From Layer 7 to Layer 1:
“All People Seem To Need Data Processing”
From Layer 1 to Layer 7:
“Please Do Not Throw Sausage Pizza Away”
Real-Life Example of the OSI Model
Imagine you’re sending a message via WhatsApp:
- Application Layer: You type and send a message.
- Presentation Layer: Message is encrypted (e.g., end-to-end encryption).
- Session Layer: A session is maintained between your phone and the receiver.
- Transport Layer: Message is broken into segments (TCP/UDP).
- Network Layer: Each segment is given IP addresses.
- Data Link Layer: Data is framed and sent to your router.
- Physical Layer: Message is transmitted via Wi-Fi or mobile network.
OSI Model vs TCP/IP Model
| OSI Model | TCP/IP Model |
|---|---|
| 7 Layers | 4 Layers |
| Theoretical Model | Practical Model |
| Developed by ISO | Developed by DARPA |
| Layers: Application, Presentation, Session, Transport, Network, Data Link, Physical | Layers: Application, Transport, Internet, Network Access |
Why the OSI Model Still Matters
- Helps in network troubleshooting
- Guides protocol development
- Essential for certifications like CCNA, CompTIA Network+
- Improves conceptual understanding of data communication
Conclusion
The OSI Model may be conceptual, but it’s incredibly useful in understanding how different components of a network interact. It breaks the communication process into 7 clear layers, making it easier to troubleshoot and optimize networks.
Understanding the OSI Model isn’t just for exams, it’s the key to mastering networking fundamentals.